Vorsicht SPAM❗ Microsoft PowerAppPortal & Valbeeek Law ⇒ mit 3 e
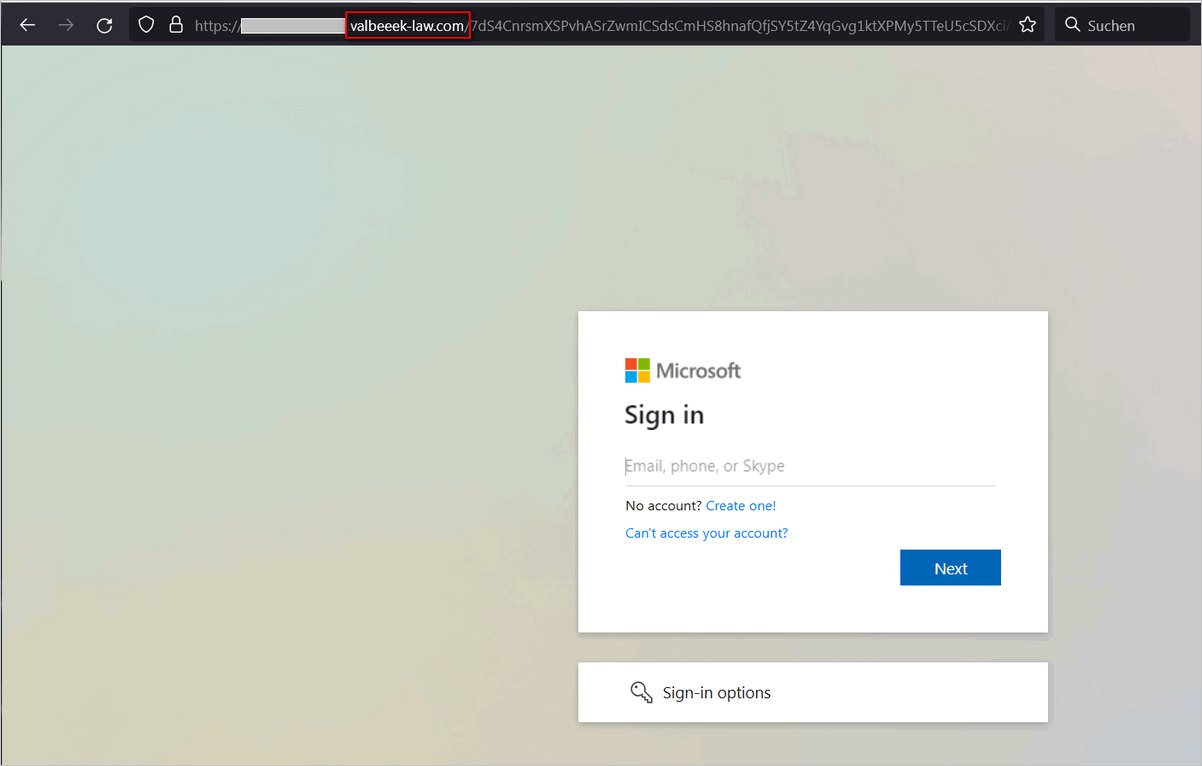
Hoch professioneller Spam der übelsten Sorte!
IT-Security

Hoch professioneller Spam der übelsten Sorte!
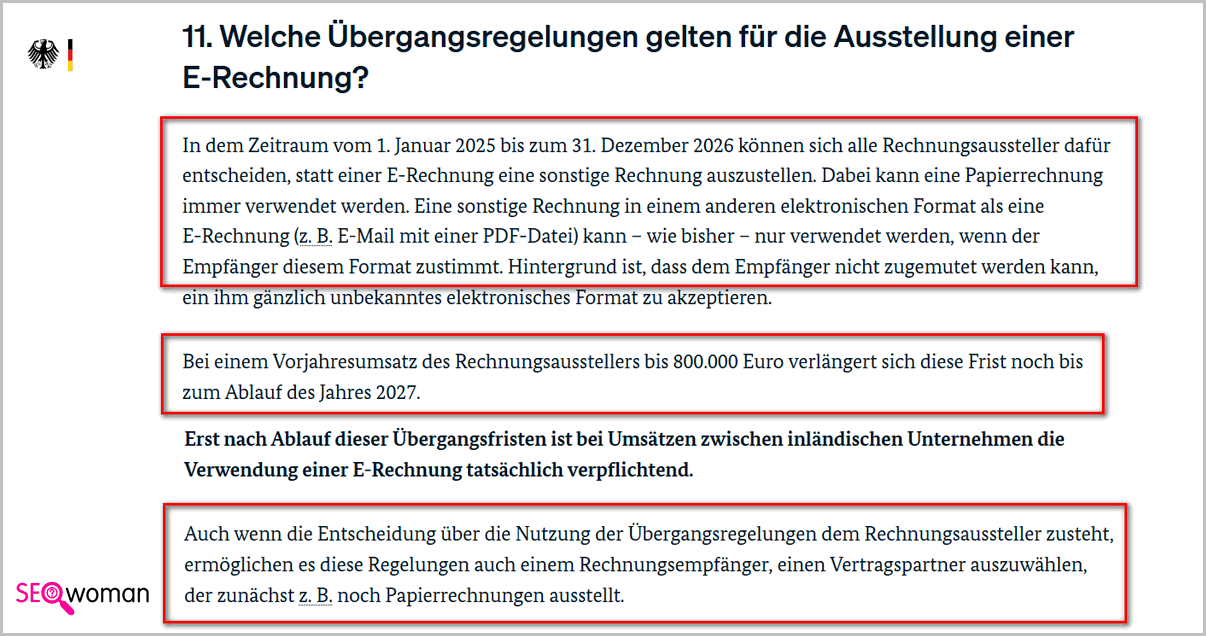
Du kannst weiter ⇒ Papierrechnung schreiben ✓ ⇒ Rechnung als PDF versenden ✓ » bis 31.12.2027 ▻ Details » mit Bildern ✚ Links

Leistungsschutzrecht ab 2012 bis Heute
Die schädliche App Xhelper greift Geräte an
Daten von Kindern unter 13 Jahren ohne Zustimmung gesammelt & für Marketing verwendet

5 Tipps für mehr Handy-Sicherheit
Google Fuchsia Betriebssystem – ein Geheimprojekt?
Die besten Videos » Die Top-7-Vorträge auf Deutsch #35C3

Du kannst alles Hacken … Du darfst dich nur nicht erwischen lassen!

Gestorben am 2. April 2019
Weißt du die MAC-Adresse deines Telefons? » Warum du deine persönliche Wanze immer dabei hast!

Wie sicher sind elektronische Patientendaten in einer App auf dem Handy?